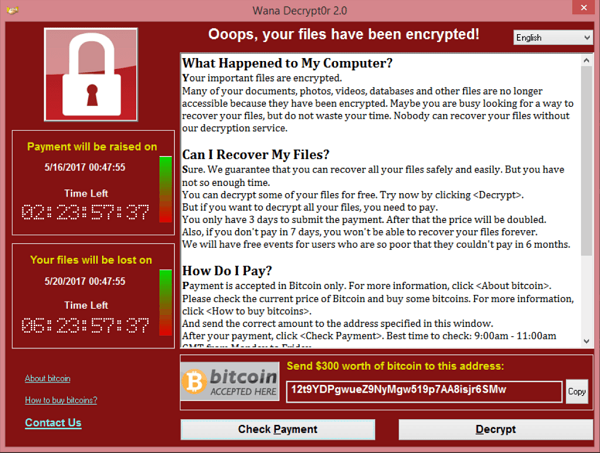
In the months since the WannaCry cyber attack on the NHS, there has been considerable speculation as to who was responsible, but now the British Government has officially blamed North Korea for the devastating ransomware attack.
Security Minister Ben Wallace stated that the Government was “as sure as possible” that a foreign state, specifically North Korea, had carried out WannaCry. This statement echoes President of Microsoft Brad Smith’s thoughts that North Korea was behind the WannaCry attack, which affected hundreds of thousands of computers in 150 countries around the world and crippled the NHS. Smith had also suggested that North Korea had carried out the attack using tools stolen from America’s National Security Agency (NSA).
The Security Minister went onto to suggest that the West should develop a “doctrine of deterrent” but stopped short of calling for retaliatory attacks.
As we discussed last week, an independent investigation conducted by the National Audit Office found that WannaCry would not have affected the NHS as badly had they had basic IT security measures in place. It has been reported in the aftermath of WannaCry that 5% of the NHS has IT systems using the 17 year old Windows XP system, which is extremely outdated in regards to cyber security.
WannaCry had a very real human impact: an estimated 19,000 operations and appointments were cancelled because of the attack. It was also only halted by accident by digital security researcher Marcus Hutchins. This leaves us facing the question: as these cyber attacks become more refined, what happens if the next one proves harder to stop?
How Cyber Essentials Can Help
The first step to keeping your organisation safe from potential future cyber attacks is to be certified with Cyber Essentials.
Certification to the Government’s Cyber Essentials Scheme is a mandatory requirement for organisations wishing to win business with the MOD, and can help your organisation prepare and defend itself against malicious cyber attacks, regardless of the sector you operate in.







