Over the past several weeks various large and small organisations both in the public and private sector have become victims of Cyber attacks. Today news is circulating that on a global scale business are being infected once again with a cyber attack nicknamed Petya prompting many onlookers to label this a potential repeat of WannaCry.
This instance appears to be having a devastating impact across Ukraine with Banks, Airports and Utility companies reporting multiple breaches. Here in the UK British advertising heavyweight agency WPP says it has experience some IT disruptions.
The Chernobyl nuclear power plant has also had to monitor radiation levels manually after its Windows-based sensors were shut down reports are indicating which sheds more light on the US software giants security.
Experts suggest the malware is taking advantage of the same weaknesses used by the Wannacry attack last month and is being referenced as a Wanna Cry 2 in some circles.
“It appears to be a variant of a piece of ransomware that emerged last year,” said computer scientist Prof Alan Woodward talking to the BBC.
The NCSC has been quick to react and has posted the following statement regarding the global ransomware incident:
The NCSC website provides advice to the public and business on how to protect your digital systems.”Read the NCSC’s ransomware guidance for organisations.
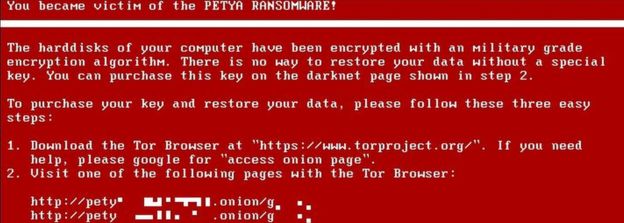
What is Petya/Petrwrap?
By: Prof Alan Woodward, University of Surrey
Petya is a type of ransomware that appeared in early 2016 and returned to a trick first seen in the early 1990s, whereby criminals do not encrypt all the files on your computer but instead they attack a part of the operating system called the Master File Table (MFT).
The MFT is essential for the system to know where to find files on the computer, so it has the same effect as if each file had been locked separately.
The big difference is that it is very much faster to attack the MFT than to encrypt each file separately.
In early 2017, a new form of Petya, dubbed Petrwrap, emerged which built on Petya but it corrected some of the weaknesses in the original code that allowed security companies to help people unlock their systems.
Whilst Petrwarp is detectable by antivirus checkers, if it manages to gain a foothold before it is stopped its encryption is so strong that you are unlikely to be able to break through to recover your files.
Now it appears that whilst the initial attack is probably still via something such as an infected spreadsheet arriving in an email, it can spread, at least in part, across a network using what appears to be the same weakness as was used in the Wannacry ransomware outbreak.
The above extract regarding Petya was originally posted here.
Don’t forget with DCI Cyber Essentials you can begin the steps today to protect yourself today from around 80% of today’s forms of Cyber Attacks including ransomware such as Wanna Cry and Petya. Simply click here to get started.








